AWARE FOR INSIDER RISK
Proactively reduce insider threats across the enterprise
Automatically identify and mitigate human behavior risks in collaboration tools like Slack, Teams, and Zoom
Protect your organization and your people with automated insider threat detection that works 24/7 to flag risks in real time and accelerate time to detect and contain.
Improve risk posture
Proactively identify malicious or negligent insider events and reduce time to detect and contain through automated policies.
Mitigate costly fines
Shield your data from malicious insiders and threat actors and preserve information security and compliance measures.
Protect your culture
Real-time insights help identify toxic employees, disgruntled behavior, and flight risks—before they cost your organization.
What can you do with Aware?
Address the blind spots of complex collaboration datasets
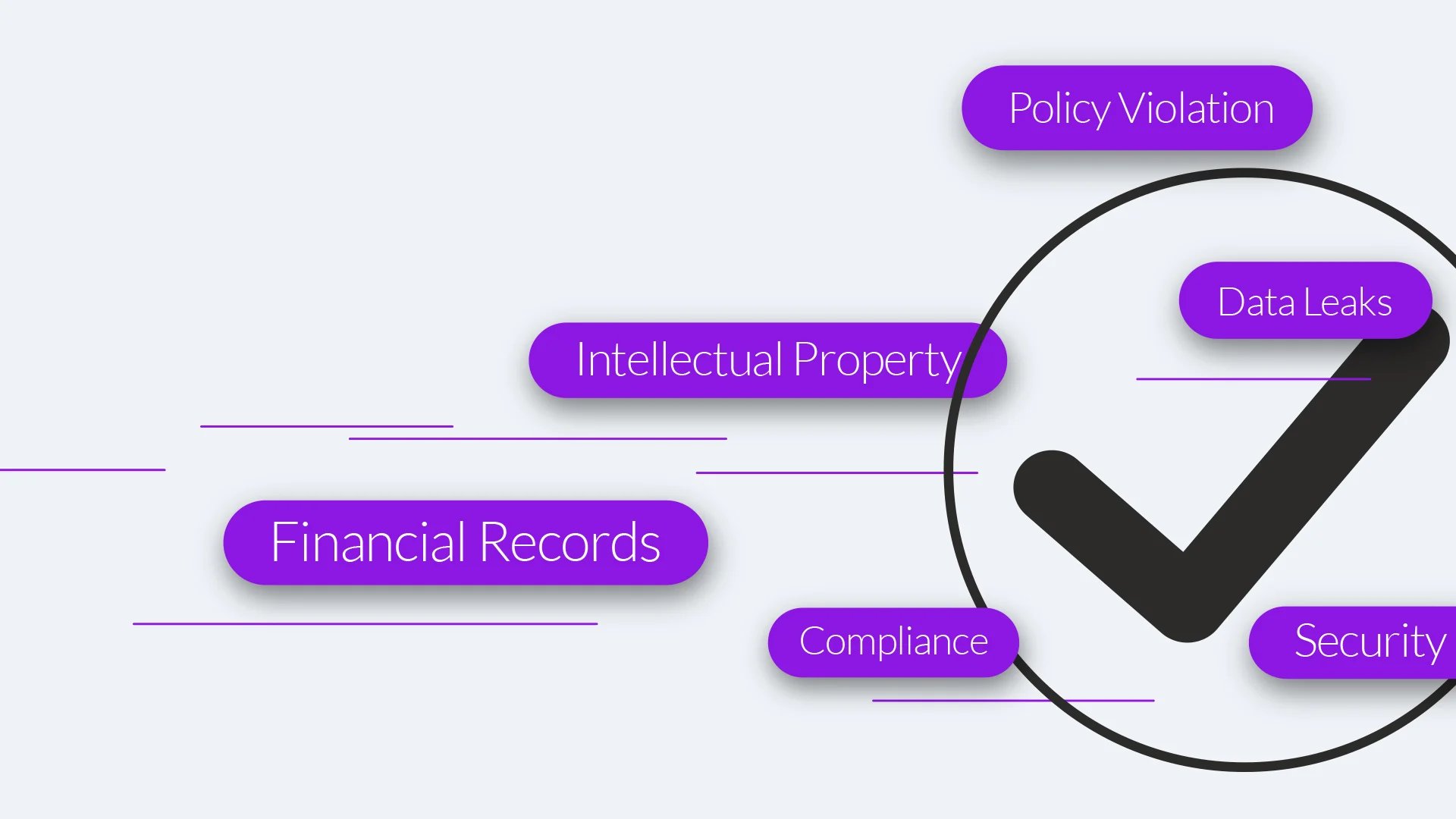
Gain the ability to see around corners and highlight risky activity such as unauthorized information-sharing, file uploads, or code sharing with AI-infused activity analysis normalized for your organization.
Reduce false positives and accelerate time to resolution
Customize automated workflows to surface the information and behaviors that matter most to your organization and reduce false positives with smart filters that pinpoint the greatest risks.
Understand the cause, effect, and impact of insider threats
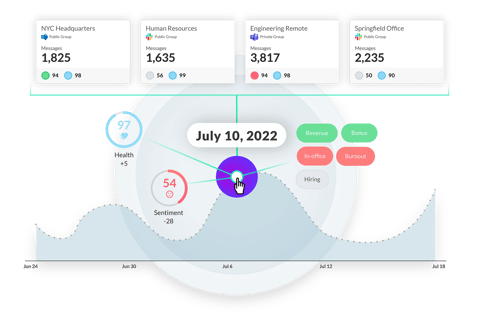
Aware delivers complete, contextual oversight of the who, what, where, when, how, and why of insider risk in collaboration for better understand of what went wrong and how it impact the org.
Around-the-clock automated insider threat hunting
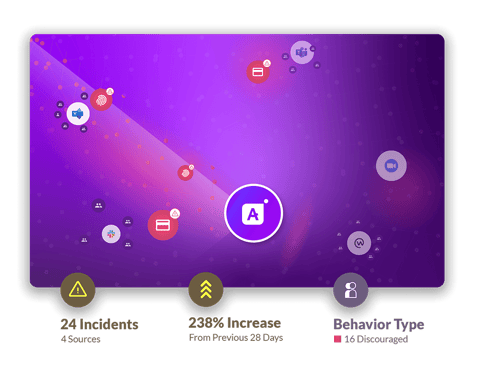
Protect your business from malicious insiders with automated threat detection normalized for your organization. Review and assess insider risks across collaboration tools like Slack, Teams, and Zoom and manage your entire ecosystem from a single centralized platform.
SIGNAL
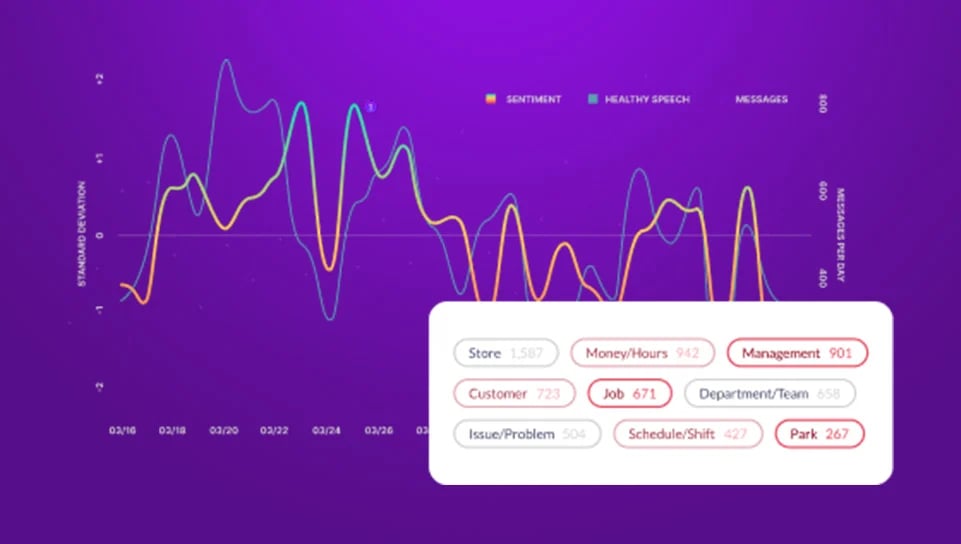
Ingest and analyze collaboration messages in real time with customizable workflows that immediately flag risky results for review for fast, accurate insider threat detection.
- Automated workflows run 24/7 to monitor messages in real time
- Configure workflows based on a wide range of AI-enhanced filters
Spotlight
Automatically surface negativity and toxicity — the warning signs of insider risk — and address them in real time to lower threat levels and defend your company cultur
RESOURCES
See how Aware can help you proactively reduce insider threats across your enterprise
Whitepaper
The Human Behavior Risk Analysis
Uncover the truth about human behavior risks that live in collaboration tools and learn how to address them before they get out of control.
-1.webp?width=1920&height=1080&name=Aware-Webinar-PeoplePerimeter-ResourceImageThumbnail%20(1)-1.webp)
Webinar
People as the Perimeter in Collaboration
The new world of work doesn’t exist behind firewalls, but on devices your employees carry 24/7. Here’s what you need to know to keep your data safe.
Frequently asked questions
What is insider risk?
Insider risk refers to the threat posed to organizations by their employees, contractors, or partners. Anybody with authorized access to assets, systems, or data can become an insider threat. Not all insider risk is malicious — human error accounts for a significant percentage of all insider threat incidents. Inadvertent insider risk can be caused by actions such as clicking on phishing emails, accidentally sharing proprietary files in public collaboration groups, or gossiping about confidential information. Malicious insiders set out to deliberately sabotage the company and usually cause the most damage. Detecting a malicious insider can be difficult, and the longer they remain unnoticed, the more damage they can do. Malicious insider threat includes actions such as stealing company secrets and planting malware.
What is the most common type of insider threat?
According to the Verizon Data Breach Investigations Report, negligent insiders are by far the most common insider risk to any organization, responsible for 62% of all data security incidents. Malicious insiders are responsible for just 14% of insider data breaches. The remainder of cases involved stolen credentials.
Despite being more common, negligent insider threats are typically the least damaging to the enterprise. The average cost of remediating insider negligence was just over $300,000 in 2020, compared with over $750,000 when a malicious insider was the cause of a data breach. Malicious insiders can do more damage by deliberately targeting a company’s most valuable data and evading attempts to be identified.
Overall, insider risk of all kinds is responsible for just 20% of data breach incidents. The other 80% involve external threat actors. However, the cost of remediating an insider breach is much higher — the average insider exfiltrates 10 times more information than the average external threat actor.
What are collaboration tools? How are they different to other business communications?
Collaboration tools are software applications that enable individuals and teams to work together more effectively and efficiently. These tools are designed to facilitate communication, document sharing, project management, and workflow automation across the enterprise. Top collaboration tools include Slack, Microsoft Teams, Webex by Cisco, Zoom Team Chat, Google Drive, Workplace from Meta and more.
Collaboration tool data differs from traditional business communications in several key ways. Emails are highly structured, defining who sent and received their contents. They create linear chains of communication that are simple to follow. By contrast, collaboration datasets are much more complex, with conversations flowing seamlessly between public, private, and group chats. Collaboration messages can also be revised or deleted, which is rarely possible once an email has been sent. The Aware platform was built for and normalizes collaboration datasets, adding critical context that would otherwise be lost.
Are collaboration messages private? Can third parties see company collaboration chats?
The privacy of collaboration messages depends on how they are sent and stored, and what settings or third-party applications the workspace owners implement. In general, direct message conversations between two users are private and can only be seen by those users. However, messages sent in public channels or private groups can be seen by all members of that channel or group. If a company collaboration tool allows external vendors to be added to channels or groups, that third party can also view all the messages they contain. Additionally, workspace owners and administrators can gain access to all the content in their collaboration tools, including messages, files, and other data. Employees should follow company policies governing the appropriate use of collaboration tools and use best judgment when sharing or uploading information within collaboration conversations.
What damage can a disgruntled employee do in collaboration tools?
Disgruntled employees are a rising concern to modern enterprises. They are workers who are unhappy, dissatisfied, or resentful in their job. They can pose a significant problem for organizations, as they may become unproductive, engage in negative behaviors, or even actively work to harm the company's reputation or operations.
Collaboration tools open up new opportunities for toxic or disgruntled employees to disrupt or even sabotage the organization. Because collaboration tools can sync messages and files in real time across multiple devices, they make it much easier to exfiltrate information. All a disgruntled employee needs to do is send themselves a sensitive file in a collaboration message, sync that message through their phone or personal computer, save the file and delete the message. If organizations do not deploy a platform like Aware that ingests collaboration messages in real time, that entire transaction can go undetected.
Another risk posed by collaboration tools is in the data they contain. Sales tactics, intellectual property, merger and layoff conversations are common to most company collaboration datasets. In addition, legally protected information such as personally identifying information (PII), protected health information (PHI) and payment card industry (PCI) data can all exist in collaboration datasets unless an organization takes proactive steps to detect and remove them. Aware enables this functionality with real-time AI/ML workflows that automatically identify and flag sensitive information within collaboration.
How does Aware support insider risk detection in collaboration?
Insider risk can be hard to detect in any organization, but disgruntled employees do make themselves known through their actions. Aware built the industry’s leading natural language processing (NLP) and sentiment scoring models, built for the nuances of collaboration datasets and trained on millions of real collaboration messages. As Aware ingests collaboration data, artificial intelligence workflows analyze and score the sentiment of messages and deliver results normalized for each individual organization. That sentiment scoring provides greater insight into how the mood shifts within the organization, where negativity is strongest, and where toxicity starts to take hold. These insights enable organizations to be proactive about addressing areas with a high potential for insider risk.
What types of insider threats can Aware detect?
Because insider risk comes in many forms, Aware provides a wide range of configurable workflows to identify and take automatic action on insider threats. These include automated workflows to detect personally identifying information (PII), protected health information (PHI) and payment card industry (PCI) data using regular expressions (regex) and Boolean logic. Aware also uses AI analysis to detect password sharing in collaboration, and each organization can create customized workflows that target specific insider knowledge and proprietary information.
Aware can further identify unsanctioned use of collaboration tools based on data type, for example sharing code snippets or restricted files can also trigger automated workflows. And Aware’s industry-leading natural language processing (NLP) models support early identification of harassment, bullying, hate speech and toxicity within collaboration tools.
What collaboration tools does Aware support?
Aware supports all major collaboration tools, including Slack, Microsoft Teams, Webex by Cisco, Zoom Team Chat, Google Drive, Workplace from Meta and more. See our Integrations page for a comprehensive list. Thanks to Aware’s Context API, enterprises can also connect their own workplace collaboration solutions with Aware’s intelligent data fabric, providing insights and analysis to almost any collaboration dataset.
What other use cases does Aware support in addition to insider risk?
Aware was built to help innovative companies mitigate risk and realize the value locked within their collaboration tool data. Aware ingests collaboration messages in real time and infuses them with intelligent analysis that reveals the hidden context of how modern businesses run. From Aware’s contextual archive, businesses can access a range of use cases, including: data loss prevention (DLP), forensics and investigations, compliance adherence, eDiscovery, employee experience, toxic hot spot detection, information governance, business feedback loops and key initiative tracking.